
When we talk about network security, security risks associated with routers is a major concern among users. A router, whether it’s wired or wireless, is an integral part of any home or business network. However, wireless routers or Wi-Fi routers are considered to be less secure than wired ones, but that doesn’t necessarily mean you should avoid wireless networks. In fact, wireless networks have many advantages over wired networks. If your wireless router is configured correctly, it can be virtually as secure as a wired setup.
Network: A computer network is a group of computers and other devices (such as a printer) connected together so that they can communicate to each other and share data across different computers within the network
Router: A router is a networking device that connects multiple networks together and forwards data packets from one network to another.
Why do You Need a Wireless Router?
Today, most modern networks consist of a diverse range of computing devices from Ethernet-only desktop computers to Wi-Fi enabled mobile devices, such as tablets and smartphones. In order to connect all these devices so that they can communicate seamlessly with each other, and share a single Internet connection, having a Wi-Fi router is the only real-world solution.
Security Risks Associated with Unsecured Wireless Router/Network
Whether you are using a wired router or a wireless one, if it is not configured properly, both of them could pose potential security risks. The common notion that wireless routers or networks are not secure or less secure is true, but only in circumstances where it is used right out of the box without correctly configuring its security settings. If your wireless network is ‘unsecured’ or ‘open’, an intruder can easily gain access to your internal network resources as well as to the Internet, all without your consent. Once the intruder has access to your network, he/she can use it for a variety of operations, such as:
- To steal your Internet bandwidth.
- To perform disruptive or illegal acts.
- To steal your sensitive information.
- To perform Denial-of-Service (DoS) attacks to make the network unusable by sending out false requests.
- To infect the network with malicious threats.
What Security Features Make a Wireless Router Good?
Since its inception, wireless routers have gone through several improvements and security enhancements. Most of the wireless routers on the market today support multiple levels of encryption and offer several security features to help protect your wireless network. Some crucial features include:
- Network Address Translation (NAT) : The NAT feature on your router separates your internal network from the Internet. Your router acts as an interface between the global public WAN (Internet) and your private local network. Certain attacks against operating systems like Windows require that the attacker communicate directly with the computer. When a machine is behind a router employing NAT, those attacks go to the router and no further.
- Built-in Firewall: The built-in firewall feature on your router acts as a robust entry-point protection which distinguishes legitimate traffic from unsolicited traffic and rejects uninvited inbound connections.
- Integrated Threat Defense: A router with the integrated threat defense feature provide an entry-point level of protection against malicious attacks threats such as worms, viruses, spyware, etc.
- WPA2 Security Encryption: Make sure the wireless router you have, or are planning to purchase, supports the WPA2 encryption method. WPA2 provides the most secure encryption over WPA and WEP.
Recommended Security Setup
No matter how good your wireless router is, in order to have a secure network you must change the router’s default settings and configure it properly. Here are few recommended security settings that you should consider while setting up your router:
Note: All screenshots that you see below are captured from the Linksys WAG120N router’s configuration page. Yours may look different!
1. Change Login Credentials: The very first thing you should do on your router is to change its default login credentials. Router’s come pre-configured with a default username and password to allow users access the router’s control panel. The login credentials set by the router manufacturer are all the same (usually admin/admin or admin/password) and is available in the user’s manual and other publications. Consider using a strong password (combination of alpha-numeric characters and at least 8 characters long), but easy for you to remember.
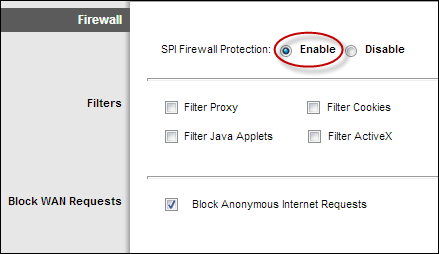
2. Enable Router Firewall: If your router has a built-in firewall, make sure it’s activated. This will enable your router to examine incoming packets and reject any unsolicited traffic.
3. Enable WPA2 Encryption: Login to your router’s configuration page and enable the strongest support encryption method. Most modern wireless routers these days support multiple levels of encryption ranging from WEP (Wired Equivalent Privacy), WPA (Wi-Fi Protected Access) to WPA2 encryption. WPA and WPA2 provide stronger authentication and encryption over WEP. WEP is the oldest and least secure encryption method and should be avoided.
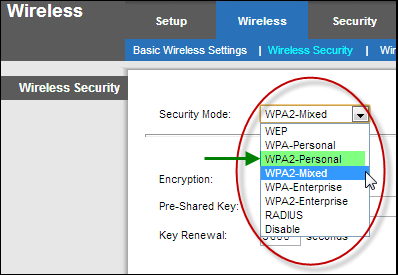
We recommend using WPA2 encryption as it is the most recent and has the strongest encryption method available. The WPA encryption method comes in personal and enterprise versions. On the other hand, WPA2 comes in personal, mixed and enterprise versions; we have listed a brief description of all the WPA2 versions below:
- WPA-Personal/WPA2-Personal: These security modes are well suited for home and small office network environments. Both of these modes use Pre-Shared Keys and do not require an authentication server.
- WPA-Enterprise/WPA2-Enterprise: As the name suggests, these two security modes are designed for enterprise-class network needs. These security modes require a RADIUS (Remote Authentication Dial In User Service) authentication server and use Extensible Authentication Protocol and provide added security. Setting up a WPA-Enterprise or WPA2- Enterprise can cost a lot and the implementation can be complicated.
- WPA2-Mixed: This security mode allows clients to use either WPA-Personal or WPA2-Personal. WPA2-Mixed mode permits the coexistence of WPA and WPA2 clients on a common service set identifier (SSID) to allow older wireless devices to connect to the network using TKIP or AES encryption methods.
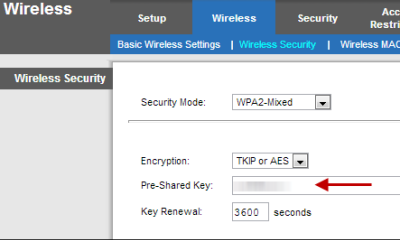
Whether you use the WPA or WAP2 encryption method, make sure to use a strong, complex, and difficult to guess Pre-Shared Key (Password). Please note that Pre-Shared Key is different from your router’s login credentials. Your router login credentials are required to access your router’s configuration page, whereas the Pre-Shared Key is required by wireless devices to join your network. This password can even include spaces so feel free to make a little phrase here.
4. Change SSID: Apart from changing your router’s default login credentials and IP address, you should also consider changing the router’s default SSID. SSID is a unique name that identifies your wireless network. Router manufacturers set a default SSID which usually is a combination of the manufacturer’s name and the model number. For example, Linksys®_WAG120N.
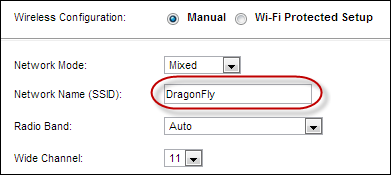
If your wireless network broadcasts the default SSID, intruders can easily distinguish the make /model of your router, and hack it with very little effort. Along with changing your router’s username, and password, it is important that you give a unique name for your wireless network.
5. Limit Wireless Coverage: Most wireless routers’ default settings extend the wireless coverage beyond your home or business perimeters. Limiting your wireless router’s coverage range could be an additional security measure to avoid probing by intruders outside your network coverage area. Please note that this is not a common feature on majority of routers. If you router has this feature (a few manufacturer’s call this feature ‘Radio Power’), you can use it to achieve this goal.
6. Do NOT Disable SSID Broadcasting: Unlike most guides that you might have read before, we do not recommend disabling this feature. When you disable SSID broadcasting on your wireless network, your wireless network will not show up when you search for a wireless network on Wi-Fi capable mobile devices. The idea is to hide your wireless network so that intruders and unauthorized persons wouldn’t know you have a wireless network! It sounds like a good idea, but it doesn’t offer any significant security advantages.&
Any determined hacker can still sniff out your SSID, and in most cases, hackers don’t even need to have your SSIDs in order to get into your network. Disabling SSID broadcast means you will have to manually configure Wi-Fi connections on new wireless devices that you wish to join your network. This could be a major inconvenience.
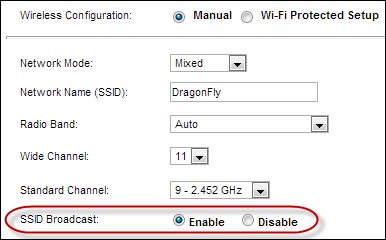
7. Do NOT Disable Universal Plug ‘n’ Play (UPnP): Again, unlike most guides, we do not recommend disabling the UPnP feature either. UPnP is a very useful router feature that dynamically opens virtual ports for applications when they need one. A virtual port allows software and devices to have a direct connection to the Internet for very specific purposes. An Xbox 360 may open a port for a multiplayer game, for example. Disabling this feature means that you would have to manually open all ports of all programs you will be using.
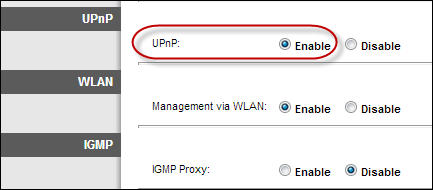
NOTE: Please note that some routers could have security issues related to UPnP. However, you can always verify if your router is vulnerable by visiting the following website: https://upnp-check.rapid7.com/
Unfortunately, if the result says your router is vulnerable, you should contact your router’s manufacturer to verify if there is a firmware update available. Router manufacturer’s often release firmware updates to address security vulnerabilities and offer product enhancements. If there is no firmware update available, you should consider replacing your router.
Warning: Updating router firmware is a critical process and we recommend that you seek assistance from a qualified technician.
Every system has a flaw, but that doesn’t necessarily mean you should avoid it. With just a few security measures, you can enjoy your connected home or business network.
If you have any questions related to home networking, feel free to share it with us on our Facebook Page, or simply leave a comment below.
Copyright © 2013 Support.com, Inc. All rights reserved. Support.com is a trademark or registered trademark of Support.com, Inc. in the United States and other countries. All other trademarks are the property of their respective owners.

This is so good and comprehensive. Thank you. Here’s my blog: https://ducktoes.com/blog
nice
piece of information, I had come to know about your internet site from my
friend vinay, delhi,i have readatleast 12 posts of yours by now, and let me
tell you, your website gives the best and the most interesting information.
This is just the kind of information that i had been looking for, i’m already
your rss reader now and i would regularly watch out for the new post, once
again hats off to you! Thanx a ton once again, Regards,https://trendjobhubs.blogspot.in/