In a stunning cyberattack, reminiscent of the 2014 Sony Pictures breach, Disney has been hit by a major hack. This attack, carried out by the well-known hacker group NullBulge, has exposed huge amounts of Disney’s internal communications and sensitive data. The breach specifically targeted Disney’s Slack channels, resulting in the unauthorized release of roughly 1.2 terabytes of data.
The infiltrated data encompasses nearly 10,000 channels, encompassing every message, file, and conversation possible. NullBulge declared on X, formerly Twitter, “1.2 TB of data, almost 10,000 channels, every message and file possible, dumped. Unreleased projects, raw images and code, some logins, links to internal api/web pages, and more! Have fun sifting through it, there is a lot there. We tried to hold off until we got deeper in, but our inside man got cold feet and kicked us out! I thought we had something special {name}! Consider the dropping of literally every bit of personal info you have, from logins to credit cards to SSN, as a warning for people in the future.”
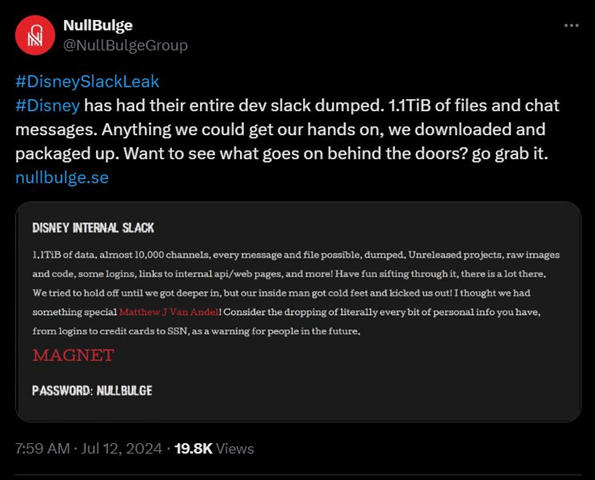
This attack highlights the vulnerability of corporate communication platforms such as Slack. The leaked data was comprised of many elements, ranging from unreleased projects to raw images and internal codes – all of which could be disruptive in relation to Disney’s future operations. It could be argued that the more costly element of the leak was the exposure of sensitive login details and internal APIs, further exposing Disney’s cybersecurity infrastructure.
Disney were quick to respond to the hack, announcing that they had quickly launched a thorough investigation to uncover the true cost of the breach. Disney themselves have admitted to the breach and announced that they are taking steps to prevent a repeat of this in the future.
It is worthwhile stepping back and assessing the wider picture when it comes to data breaches. It is often only when newsworthy corporations such as Disney are compromised that discussions around cybersecurity are truly brought to the fore. However, these attacks happen on a daily basis and businesses of all sizes are targeted. In 2023, the average cost of a data breach in the U.S. was an astonishing $9.48 million, while globally it was $4.45 million. It is not just the financial consequences of such breaches that are harmful to a business, but also the reputational damage that they cause. Numbers such as these serve to highlight the importance of a robust, all-encompassing cybersecurity strategy. At the forefront of this should be a comprehensive, business-wide antivirus software that is easily manageable through a single site license, such as SUPERAntiSpyware’s business antivirus software offering.





 What Are Cookies and How do they work?
What Are Cookies and How do they work? Top 5 Google Chrome Extension Picks For Better Web Security
Top 5 Google Chrome Extension Picks For Better Web Security