Hancitor, also known as Chanitor, is known for dropping its payloads rather than downloading them post-infection, as well as for a unique phishing approach to trick users into downloading and activating Microsoft Word documents with malicious macros.
How it works
Hancitor uses a new template that attempts to fool the user into believing that it is a FedEx tracking number. There is no attachment, however; instead, the tracking number link directs the user to the sjkfishfinders[.]com domain and then downloads the Word document. Once downloaded, the Word file attempts to trick the user into allowing macros, which would trigger code residing inside the file. An example can be seen below:

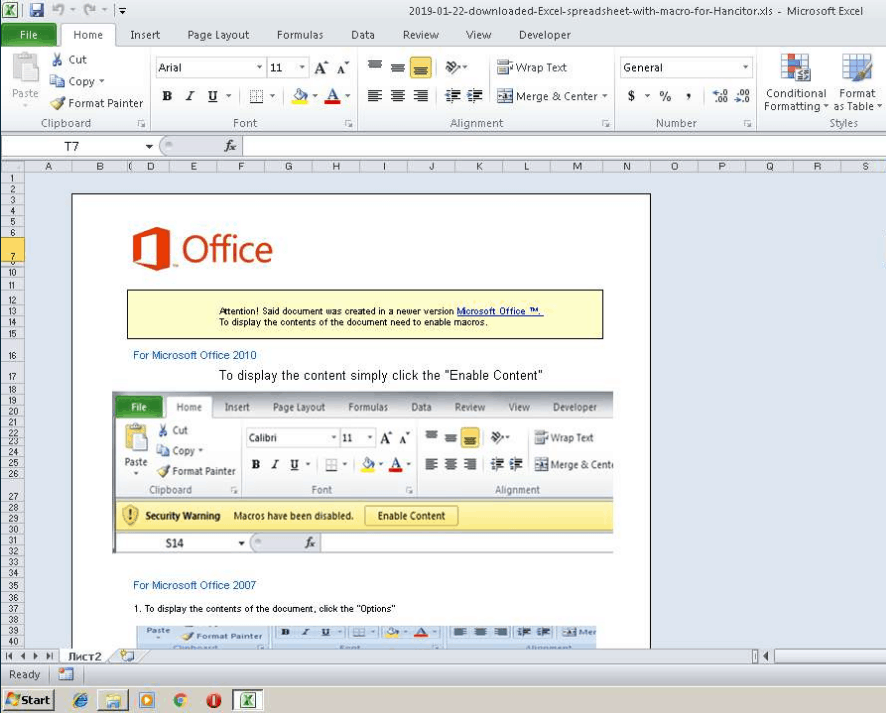
The lack of an attachment, often seen as a red flag by many users, may lure the user into a false sense of security. It is important to be careful about which links you click: on most modern web browsers, hovering your mouse pointer over the link will tell you where the link will lead to. If you do not know the address, then it is safer to avoid following the link.
When a user enables the macro, rather than download the application from the internet, the application it is instead extracted from inside the document and dropped in the hidden folder \AppData\Local. Before finishing, the script launches the command cmd.exe /c ping localhost -n 100 && C:\Users\admin\AppData\Local\Temp\6.pif. Ping is used to delay the attack to avoid automatic detection by waiting for approximately 100 seconds before running the dropped application 6.pif. 6.pif then reaches out to a C&C server before downloading new malware or running commands.
In addition to 6.pif, another file is dropped at C:\Users\admin\AppData\Local\Temp\6fsdFfa.com.
This executable is a banker. Immediately after being run, it reaches out to api.ipify.org, which returns the
victim’s public IP address. It then attempts to submit several unique values
and the IP address in plain text to a list of infected servers. If the infected
servers reply back indicating that they are available to receive the data, the
program will begin compiling all the
usernames and passwords it can obtain and submit them to the server.
Other templates have been used by Hancitor in the past, including but not
limited to: divorce papers, parking tickets, and FTC claims. As always, its
important to have Microsoft
Office macros disabled unless required by your job.
Who is affected?
Anyone with an email address can become a target of this mal-spam campaign. While it does not use victims’ email addresses like Emotet does, Hancitor’s unique templates are meant to catch even savvy users off guard, regardless of whether the email is used for work or is a personal email.
Indicators of Compromise
- cmd.exe /c ping localhost -n 100 && C:\Users\admin\AppData\Local\Temp\6.pif
- sha256: 76b96c8d796cfcebff34d42e65e5a4ab2770fda42ea3c259097ee068660dfcc2
- md5: 4d4e366b0813148f12fa1a2638c43f72
- C:\Users\admin\AppData\Local\Temp\6fsdFfa.com
- Felighevengna[.]com
- api.ipify.org
- verrestofred[.]ru
- 81.171.7.39
- 54.204.36.156
- 95.169.184.23
- felighevengna.com/4/forum[.]php
- verrestofred.ru/4/forum[.]php
What you can do
If you or someone you know is infected with Hancitor
malware download SUPERAntiSpyware Professional right now and get a 14-day free trial, no
credit card required. SUPERAntiSpyware is easy to install and will detect
and remove Hancitor from any Windows computer.
If you are a Computer Technician, you may like to try our SUPERAntiSpyware Tech Edition solution, now free for the next 30 days. Use Tech04 as the Tech ID. Click here: https://www.superantispyware.com/technician-download.html
How To Remove Hancitor
- Restart the infected computer in safe mode without networking.
- Search through the items in the Indicators of infection section above and investigate any files/folders you do not recognize. You can run the file through SUPERAntiSpyware or online through VirusTotal.com to confirm that it is malware.
- Delete files and folders that have been confirmed as malware.
- Repeat steps 1-3 on all other machines in the network.
- Restore all infected computers to normal mode only after confirming the infection is removed.
