
The modern malware landscape is huge, and it’s growing more and more sophisticated every day. In one of our previous blog posts, we discussed the different types of malware, their infection mechanisms and how they act within a system. Currently, there is one category of malware that is becoming increasingly more popular called “ransomware.” In this blog post, we will discuss what ransomware is and what strategies and techniques are used in creating and propagating this latest trend in internet crime.
What Is Ransomware And What Does It Do?
Ransomware is a category of malware which disables the functionality of your computer by restricting your access to it in some way. Then, it demands a ransom to be paid to the malware author to restore the system’s functionality. The ransomwares program usually locks a computer and displays various law enforcement images to intimidate and extort money from victims. In addition to locking you out of your computer, some ransomware will encrypt and hide your personals files so that you don’t have access to them anymore.
A Little Background About Ransomware
Ransomware is not a new phenomenon. The first instance of ransomwares appeared back in 1989 which was known as the PC Cyborg Trojan (also known as Aids Info Disk (AIDS)). The infamous Trojan replaced the autoexec.bat file on the infected machine and would count the number of times a computer had booted. Once the system’s boot count reached 90, the Trojan would hide directories and change all of the filenames on the drive C:\, making the system unusable. To restore the system’s functionality, the Trojan demanded that the user pay $189 to the “PC Cyborg Corporation.” Although ransomware is not new, it has drastically increased since 2005. Ransomware attacks were initially popular in Russia, but over the past few years, the number of ransomware attacks has been increasing worldwide.
Ways Ransomware Gets Into Your Computer (Delivery Methods)
Ransomware can infect your computer in the same way as most other malware. Some of the most common ways your computer can become infected with ransomwares are:
- Drive-by download: This is the most common way for ransomware to get into your computer. All it takes is for you to visit a malicious or compromised website, click on a malicious advertisement/link, or open a malicious attachment for your computer to be infected.
- Exploiting program vulnerability: Just like any other malicious program, ransomware can exploit security vulnerabilities on your computer’s operating system or in a program (such as a web browser) that has been installed on your computer.
Popular Ransomware Variants (Infection Methods)
As mentioned above, there are many variants of ransomwares out there, but it can be loosely classified into four categories:
1. SMS Ransomware: This type of ransomwares locks your computer and displays a ransom message with a code. To unlock your computer, you are instructed to send the code via text message to a premium-rate SMS number to receive the corresponding code to unlock it.
Figure 1 is an example of a lock screen (which claims to be from Microsoft) displayed by one of the SMS ransomware variants. The lock screen instructs victims to send a code (4121800286) to 3649 (which is a premium-rate SMS number) in order to receive the Windows® activation code.
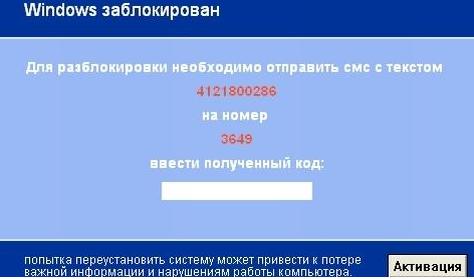
Figure 1: Example of a SMS ransomware lock screen.
2. Winlocker: This variant of ransomware also locks your computer, but it displays a more intimidating ransom message which appears to be from your local law enforcement agency. Unlike SMS ransomware, this particular kind instructs you to pay through an online payment system such as Ukash, Paysafecard, or Moneypak.
Figure 2 is an example of a recent variant of Winlocker ransomware. The lock screen indicates that the FBI has locked down the user’s computer for committing some sort of cybercrime. The lock screen also includes instructions on how the user can pay for the fine via an online payment service. This type of malware is more commonly known as the “FBI Virus” or “Moneypak Virus”.
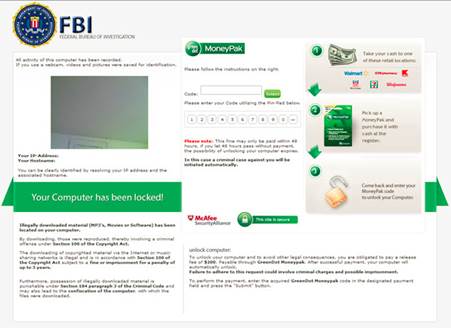
Figure 2: Example of a Winlocker ransomware lock screen.
3. File Encryptors: This kind of ransomwares can encrypt your personal files and folders using complex encryption algorithms to make your computer’s data unusable. The malware author then demands that you pay for the decryption key using one of the online payment systems mentioned above. The ransomware often leaves a file (or a “ransom note”) on the victim’s machine with payment instructions. This type of ransomwares may or may not lock your screen.
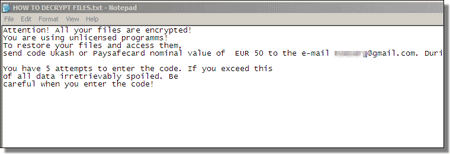
Figure 3: Example of a file encryptor ransomware ransom message/note.
4. MBR Ransomware: This is another popular variant of ransomware, but it goes one step farther than the other three types mentioned above in terms of how the computer is locked. MBR Ransomwares can change your computer’s Master Boot Record (MBR) and interrupts the normal boot process. The MBR is a partition on your computer’s hard drive that allows the operating system to load and boot. When this ransomware strikes, the ransom message is displayed as soon as the computer is turned on, meaning that you do not get the chance to load the operating system to remove the infection and repair your system.
MBR Ransomwares may look scary, but this type of infection can easily be removed. The ransom message often says that the files have been encrypted, but in reality, they are not.
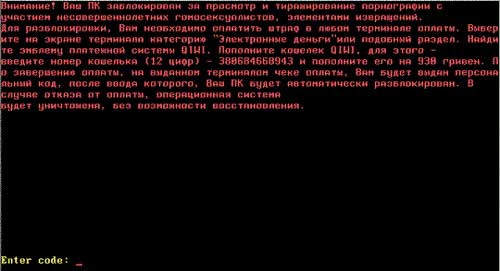
Figure 4: Example of a MBR ransomware lock screen.
How It Works
Ransomware is a profitable criminal business, and its success lies in the way it functions. The whole ransomware scheme works by scaring victims by involving law enforcement agencies and making threats of punishment and imprisonment. To give make their attack seem authentic, the ransomware authors use law enforcement logos and geo-specific services to determine the location of the computer using command and control (C&C) servers. C&C servers are centralized servers used by cybercriminals to control infected machines remotely by sending commands and receiving outputs (data) from the machines. When certain types of ransomware strike your computer, it determines which country you are in and sends that data to the C&C server. The server responds with images to be used to lock screens. These images include text written in the local language and logos from local law enforcement agencies.
How To Protect Your Computer Against Ransomwares
The ways to protect your computer from ransomware are similar to the ways to protect your computer from any kind of malware. Here are a few rules to remember to avoid malware attacks:
1. Always backup your data: Whether it’s a ransomwares or any other malware attack, there’s always a possibility of losing your data. Backup your data on a regular basis and keep those files in a secure place away from your computer so that you can restore it in an event of data loss.
2. Think before you click: Do not open email attachments that you were not expecting or click on links on suspicious websites. If you see an email from a company that is trying to get you to open an attachment to receive something like money or a parcel, ignore that email because it may be an attempt to get you to install bad software.
3. Secure your PC: Make sure your computer is protected with anti-virus/anti-malware software.
4. Stay up-to-date: Make sure that all of your security programs, operating systems and other applications are up-to-date. Also, make sure that automatic updating is turned on.
5. Don’t pay: If you believe that you are a victim of a ransomware attack, do not panic and, more importantly, do not pay. Even if you make the payment, there is no guarantee that your computer’s functionality or its data will be restored. Instead, contact your local cyber law enforcement agency.
Also, please remember that ransomware, or any other malware for that matter, is not limited to computers or Windows. For all around security, ensure that you keep all of your devices protected. If you have any questions related to this kind of malware, feel free to share them with us on our Facebook® Page or simply leave a comment below.
Copyright © 2013 Support.com, Inc. All rights reserved. Support.com is a trademark or registered trademark of Support.com, Inc. in the United States and other countries. Windows is a trademark or registered trademark of Microsoft Corporation in the United States and other countries. Facebook is a registered trademark of Facebook, Inc. in the United States and other countries. All other trademarks are the property of their respective owners.

Superantispyware is not getting rid of my Winlocker malware (says that the DOD has locked my machine) on my one user account. What else can I do?????????????