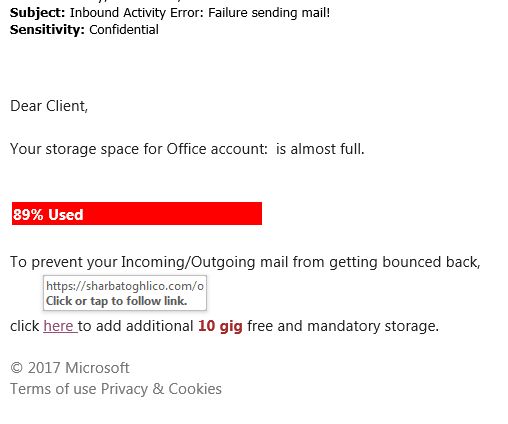
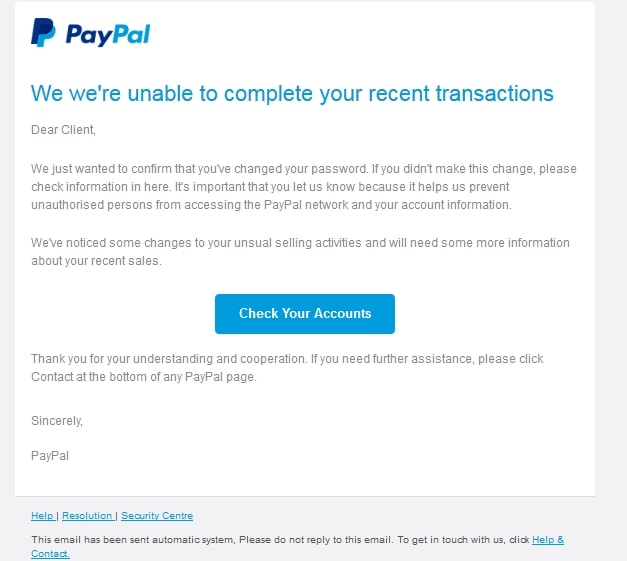
Phishing Emails Watch out for fake PayPal
We here at SUPERAntiSpyware have noticed a fairly recent clever email phishing campaign that claims to be PayPal. In the email the fake PayPal scam artists attempt to scare users into thinking that not only have their recent PayPal payments been declined, there is also unusual selling activities and they “will need some more information” about your recent sales in attempt to steal your information.
Phishing Emails
We here at SUPERAntiSpyware recommend you simply delete this email, and do not click any links within the email, especially the fake blue “Check Your Accounts” button. If you have been scammed by this email, immediately change your PayPal account password and consider looking into changing your spam settings to avoid future spam emails such as these. Remember, if you do not recognize the sender address, do not open the email, and if you do open an email such as this always hover your mouse pointer over the emails links to see where they’re trying to take you, usually phishing emails links will point you to a website that has nothing to do with the company they’re posing as.