Typosquatting is a type of internet scam that relies on end users making mistakes, such as spelling errors or entering the wrong domain name when entering a websites URL. It is also commonly known as URL Hijacking. There are many motivations for a hijacker to take the Typosquatting approach to deceiving unsuspecting victims:
1) To redirect web traffic to their own or a competitor’s product.
2) Installing malware to infect the user’s machine, typically with ad-hosting pieces of malware.
3) Freeze the web browser for a fake Tech Support scam, scaring the user into calling a fake tech support number claiming the user has a virus infection. These scams potentially cost the users hundreds of dollars.
4) To steal user information by running a phishing scheme to mimic legitimate website.
5) Making revenue from the user clicking on advertisements (either in plain site or disguised as legitimate search links) on the Typosquat website.
6) To blackmail or strong-arm payment from the company they’re Typosquatting in order to force a purchase of the website from the Typosquatter.
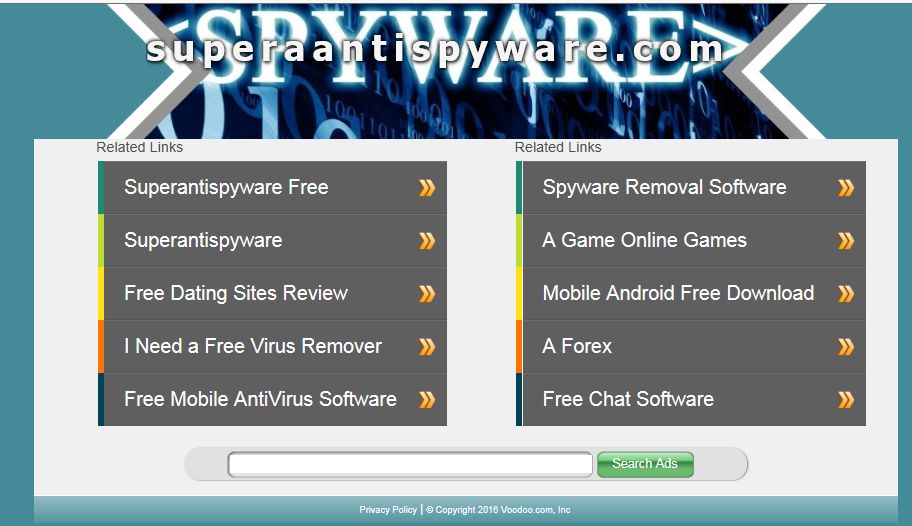
A scammer who runs a Typosquat scam typically registers a website address with spelling close to the legitimate websites address. This is typically something simple like omitting a letter, adding a letter, or using a different Top Level Domain. For example if a user wants to go to our website, they may end up typing superaantispyware[dot]com with double a’s. This will end up showing a user a Typosquatting website such as this:
Another type of Typosquat scam would be due to the person improperly typing out the full URL, typing something like google [dot] om , rather than typing google [dot] com. In this instance, the person typing the .om domain would actually be viewing a page hosted on Oman’s Top Level Domain, rather than the basic .com domain. In some instances, large corporations will buy up as many associated domains as they can in order to prevent this type of mistake (Google, for example, has variants of their site containing multiple o’s and different Top Level Domains); however, not all companies have the foresight and/or money to do this.
It is easy to avoid falling prey to a Typosquatting scam. Here are a few easy things you can do to prevent this.
1) Never open links in emails from unexpected senders, and exercise caution when visiting sites you’re not familiar with.
2) Bookmark your favorite websites so you can easily access them.
3) Use a search engine like Google, Bing, or Yahoo when looking for a specific website if you are unsure about the spelling or if the business’ website is the same as their name. Some car dealerships, for example, use dealer names or slogans as their website.
4) Double check the URL you are typing before loading the page
5) Make sure Real-Time Protection is turned on in SUPERAntiSpyware Professional
6) If you are starting a web-based business, consider buying multiple domains that are similar to your primary site to preemptively stop Typosquatters. Most domain registrars will offer bulk rates when you purchase more than one domain at a time.
While this type of attack is somewhat uncommon by today’s standards, it still happens every once in a while. By practicing safe browsing habits, keeping your web browsers up-to-date, and running regular scans of your machine, you should not be impacted by most of these types of attacks.