.png)
When it comes to spreading malware and swindling money from the victims, cybercriminals have many ways to achieve their malicious goals. In recent years, cybercriminals have become increasingly inventive in terms of writing, designing, and distributing malware. In one of our previous blog posts, we discussed about ransomware and how it is being used by cybercriminals to extort money from its victims. In this blog post, we’ll discuss about a new type of malware called ‘Rogue security software’, which closely resembles ransomware, but follows a little different approach to attack its victims.
What is Rogue Security Software?
Rogue security software, also known as rogue anti-malware, is a counterfeit software program that appears to be beneficial from a security perspective, but in reality, it’s not. Rogue security software masquerades as genuine security software, generates erroneous or misleading alerts to scare you to partake in fraudulent transactions. In simple words, the goal of Rogue security software is to deceive you into believing that your computer is infected with some serious threats, and then trick you into installing/purchasing fake security software.
While the program claims to help your computer to get rid of malware, it actually does the opposite. It stays in the system and constantly nags you about being infected and forces you into buying the solution (upgrade to the paid version of the program). One important characteristic of rogue security software is that it hooks itself deep into the system and cannot be easily removed or uninstalled.
Rogue Security Software vs. Scareware
Rogue security software is often confused with scareware. Even though both rely on fear tactics, scareware programs actually does less harm than rogue security programs. Programs like fake registry cleaners, system optimizers mainly fall into the scareware category. These programs are designed to look authentic, but do very little or absolutely nothing of what it claims. Scareware usually uses scary advertising and scary scan results to try to get you to buy something that’s essentially useless. Unlike Rogue security software, scareware programs can be uninstalled from the system easily.
Risks Associated with Rogue Security Software
Just like any other malicious threat, rogue security program also have some serious security risks associated with it. Some of the most common risks associated with rogue security software are:
1. Gives a false sense of security: The most critical risk associated with rogue security software is that the program makes you believe that the security program installed on your computer is genuine, and it will offer protection against malware attacks. To gain users’ trust, scareware authors carefully design rogue security software to look legit and functional. The program often report (using erroneous pop-up windows and security alerts) that malicious threats has been detected on your PC and the same have been removed successfully! While you think that your computer is clean and fully secured, in reality, the program provides no protection whatsoever.
2. Fraudulent transaction: Since the objective of cybercriminals who write rogue security software is to make as much money as possible, they rely on fear tactics and other social engineering tricks. In most cases, if your computer is infected with such a program, the program deceivingly alerts you that your computer is infected with serious malicious threats, and to remove them, you must register/activate the product by buying a license key. Also, the credit card information that you may provide during the purchase of license key can be used by cybercriminals to steal additional money from you.
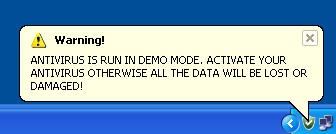
3. Interrupts legitimate security program operations: The rogue security software can even go further and disables the legitimate security programs installed on a computer or at least interrupts the functionality of genuine security programs.
4. Prevents you from visiting legitimate security software vendor sites: Rogue security software authors often write these programs in such a way that it even prevents you from visiting known legitimate security software vendor sites. This is to thwart your download attempts of a genuine security program.
How Rogue Security Software Gets into Your Computer? (Delivery Methods)
Rogue security software can strike your computer in the same way as most other malware. Some of the most common ways your computer can become infected with scareware are:
1. Advertisement: The rogue security software is a highly profitable business and to create maximum benefit for themselves, cybercriminals often carry out huge advertisement campaigns. Rogue security software programs are advertised using legitimate advertising networks to display ads on both malicious and legitimate websites, including blogs, forums, social networking websites, etc.
2. Spam Emails: Though not a very common method, cybercriminals may also use this cost-effective method to distribute their Rogue security software as a download link via spam emails.
3. Manipulated SEO rankings: Websites that distribute rogue security programs (usually developed by cybercriminals) often appears in search engine results. Cybercriminals uses aggressive search engine optimization techniques to position their malicious websites to appear in the top of search engine results. When you search for trustworthy security software or search about a recent news event, these websites may appear in the search result. Believing the website listed in the search result is genuine, when you visit the website, the website trick you into downloading rogue security software or similar programs. Thankfully, Google and the other Search Engine companies eventually remove these entries by cleaning up their results lists.
Rogue Security Software in Action: Few Examples
Below are few examples (screenshots) of rogue security software, which we hope will help you understand how rogue programs mimics legitimate program’s user interface and trick users.
Figure 1 is an example of a rogue security program known as Antivirus XP 2008. As you can see in the figure below, the rogue anti-malware is displaying false security status of the computer and encouraging the user to switch to the Full Mode (upgrade to a full/paid version).
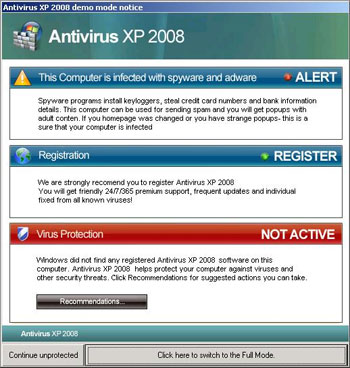
Figure 1
Figure 2 is an example of how a rogue security program is displaying a fake BSOD warning message. The message is trying to provoke fear and wants the user to register the ‘Antivirus 2010’ program to prevent data loss and damage to the computer.
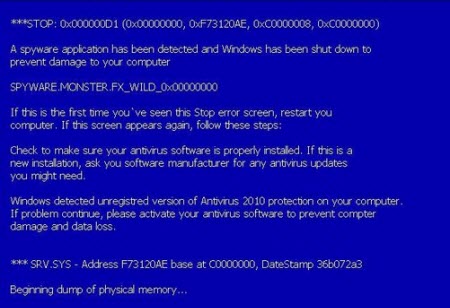
Figure 2
Figure 3 is an example of a rogue security program which is displaying a manipulated Windows® XP boot screen. Similar to example given above, it displays a message asking to register his/her copy of ‘Antivirus 2010’ program.

Figure 3
How To Tell What’s Real And What’s Not?
As mentioned earlier in this post, makers of rogue security software tries their best to mimic the look and feel of the legitimate security software programs. In fact, most rogue security programs looks so genuine and legitimate that it can even fool advanced computer users. Here are few tips that might help you in identifying rogue programs:
- Check out for spelling mistakes/poor English: One common thing among most rogue security software is the use of poor language and phraseology.
- Verify the source: If you never heard of the company before, chances are they are not legit. Search for the name of the company who makes it and read up what others have said about it. Never trust a “customer comments” page.
- Read some reviews: Spending some time searching about the program and reading some reviews can help you know more about the product.
- Consult a professional: If you are not sure whether the program you want to install/buy is genuine or not, always seek assistance of a professional.
- Take a test: Want to know how good you are at spotting the difference between a real antivirus program and a rogue program? Take the Real vs. Rogue test created by Microsoft Malware Protection Center. Please note that you need to have a Facebook account to take the test.
To Protect Your Computer Against Rogue Threats And Other Malware Attacks:
- Familiarize yourself with common phishing scams and attacks.
- Secure your PC with legitimate security programs — antivirus, antispyware, firewall, etc…
- Make sure all security programs installed on your computer is up-to-date and are always turned on.
- Think before you click on links on a website/email.
- Do a Google search for the product name before installing it on your computer.
- Do not click on ads that look scary. If the product name is not in the ad, or is trying to provoke fear, never click on it.
- Do not open email attachments that you were not expecting.
- Be careful while searching for security tools.
- Always download programs from its official source.
If you have any questions related to rogue security software, feel free to share them with us on our Facebook® Page or simply leave a comment below.
Copyright © 2013 Support.com, Inc. All rights reserved. Support.com is a trademark or registered trademark of Support.com, Inc. in the United States and other countries. Windows is a trademark or registered trademark of Microsoft Corporation in the United States and other countries. Facebook is a registered trademark of Facebook, Inc. in the United States and other countries. All other trademarks are the property of their respective owners.

I guess examples of said malware include My Clean PC, PC Matic, and Finally Fast.
When is SuperAntiSpyware Pro going to do something about Windows Security Master rougue virus or trojan what ever it is. A little to late in my opinion. I think I want my money back and I will buy something that will. I have sent you the file that it is and where to find it and filed a ticket it has been in excess of 24 hours and you won’t even respond. JUNK! I want my money back!