
How to be Safe from Phishing Today!
In today’s increasingly technology-driven world, the Internet plays a large role in spreading information. There are however things that people need to be aware of when using the Internet, such as cybercriminals, who misuse the Internet to carry out their criminal phishing attacks. They set out to deceive users into revealing their sensitive information unknowingly which can result in substantial financial loss.
Phishing attacks are one of the most serious problems that users face on the Internet and has been growing at an alarming rate. According to a report[1]published by EMC Corporation, the total number of phishing attacks launched in 2012 was 59% higher than in 2011.The global financial loss from phishing attacks is estimated to be around $1.5 billion in 2012, representing a 22% increase from 2011.
What is Phishing?
Phishing is a fraudulent act of deceiving users to acquire their sensitive personal information, such as usernames, passwords, social security numbers, and bank account/credit card details, etc. Phishing attacks are usually carried out via fraudulent e-mails, legitimate looking fake websites, fake phone calls, instant messages, malicious programs, rogue applications, etc.
How Phishing Scams Work?
It all starts with a fraudulent notification, for example an email that you receive in your inbox. The email may appear as an official request from a trustworthy company seeking to alert you to something important. Such emails are cleverly designed to look identical to the company that the cybercriminals are trying to masquerade as. Such emails furthermore contain manipulated URLs, hyperlinked texts, and malicious attachments. The emails are intended to scare/mislead you into believing that something bad has happened to your account with hopes that you act quickly by clicking on links that are included, which ultimately lead to a request for additional information to clear up the account issue.
Alongside the fraudulent emails, cybercriminals also create fake websites designed to closely resemble the official website of the company they are replicating. As soon as you click on the link in the email, you will be redirected to the fake website and you may be presented with a login screen or a web form that requests your private information. By providing your login credentials or just by filling out the form, you essentially end up handing over all your personal information. The cybercriminal at which time can misuse your information in a variety of ways including taking over your bank accounts, your credit card details, and even stealing your identity!
In phishing attacks, recipients are often tricked into installing malware on their computer, either by opening an email attachment or by clicking on a link. Once the users’ computer is infected, the malware subsequently collects sensitive information to send to criminals operating the scam.
How to Recognize Phishing Emails
Skilled cybercriminals can fool even experienced computer users. However, by being able to recognize phishing emails you may be able to reduce your chances of being defrauded:
- Your name is missing: The email doesn’t have your name in it.
- Spelling and bad grammar: The email contains spelling or grammatical mistakes.
- Threats: The email contains threats that your security has been compromised, or requests that you take immediate action.
- Seeking personal information: The email requests your personal information such as, login details, bank account details, credit card details, etc.
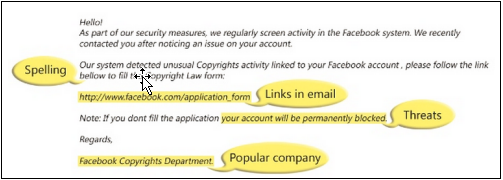
An example of what a phishing scam in an email message might look like. Source: Microsoft[2].
- Deals that sound too good to be true: The email contains deals or offers that sound too good to be true. For instance, the email claims that you have won a million dollar lottery and that they need your account information in order to credit the prize money!
- Manipulated/ misleading links or anchor text: The email contains manipulated links or deceptive anchor text that redirects you to an unreliable destination.
- Unsecured website: You clicked on a link and were directed to a website with no https:// or padlock icon.
- Donation requests: If you receive an email requesting a donation to a charitable organization after a disaster.
How to be Safeguard Against Phishing Attacks
Phishing attacks are a serious threat against all of us, and it is very important for all computer users to become familiar with various types of phishing scams as well as learn how to stay protected against them. Below is a list of top 5 ways to safeguard against phishing scams and attacks:
- Think before you act: The first step is to think before you take any action like opening attachments from an unknown sender, clicking on links included in an email, or filling out your personal information in a web form. Always be careful and think twice before doing anything on the Internet.
- Examine links and anchor text: Before you click on a link, use your mouse to hover over the link to verify the links destinations.
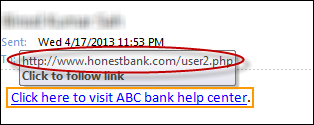 To verify a link/anchor text on a web browser, use your mouse cursor to hover over the link/anchor text to see the actual destination URL in the browser’s status bar. Alternatively, you can right click on the link > select ‘copy link location’ > and paste it in notepad.
To verify a link/anchor text on a web browser, use your mouse cursor to hover over the link/anchor text to see the actual destination URL in the browser’s status bar. Alternatively, you can right click on the link > select ‘copy link location’ > and paste it in notepad. - Never click on a link in an email if it’s supposed to take you to a sensitive website: If the email you received is from your bank, just go to your bank’s website – don’t use the link in the email. If it’s a real notification, the notice will be posted on your account as well.
- Keep your web browser up-to-date: Most modern web browsers today come with built-in features to help you stay protected against rough and malicious websites. Make sure your web browser is up-to-date.
- Keep your computer up-to-date: Keeping just your web browser up-to-date is not enough. Always make sure that your computer is up-to-date with recent operating system updates/patches, enabled firewall, and your security software has the most recent definitions.
- Make a call: If you ever receive an email from a company or an institution and you are not sure of its authenticity, do not hesitate to call the company or institution directly to verify if the email is genuine.
Phishing Attacks Are Not Limited to Emails
It is important to mention that phishing attacks via email are a common practice but are not limited. Cybercriminals are aware of the rising popularity of social networking websites and smartphones and are taking advantage of these platforms. You may become a victim of phishing attacks by clicking on a bogus post on a social networking site like Facebook, or installing a malicious app on your smartphone.
Phone-based phishing attacks are becoming more common these days. Cybercriminals often attempt to trick users into divulging personal information via telephone calls or text messages. If you get one of these, contact your financial institution directly to find out if it’s real.
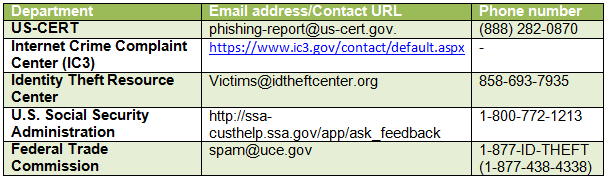
Reporting Phishing Attacks
If you believe you are a victim of a phishing attack, act quickly! Below is a list of some organizations that can assist you:
If you have any questions related to phishing, feel free to share it with us on our Facebook® Page, or simply leave a comment below.
1 https://www.emc.com/collateral/fraud-report/online-rsa-fraud-report-012013.pdf
2 https://www.microsoft.com/security/online-privacy/phishing-symptoms.aspx
Copyright © 2013 Support.com, Inc. All rights reserved. Support.com is a trademark or registered trademark of Support.com, Inc. in the United States and other countries. All other trademarks are the property of their respective owners.
